January 22, 2024
INTRODUCTION
I've been writing some of my musings since the New Year has begun and formatting some to share on this website. I'm a strong privacy advocate so there is a theme here I suppose. I make every effort possible since c. 2007 to use Free/Libre Open Source operating systems and software. I've been willing to be "inconvenienced" to exercise such liberties and have challenged myself to learn new things by doing them. Thanks to many great comments, blogs, webpages and videos online, I have learned much over the years. For example, let's say I want to learn how to make 3D images. I simply check out Blender.org and the legions of videos on YouTube. Sometimes the learning challenge is daunting, but finding just one little thing that is worth replicating and perhaps re-doing to suit some idea I may have in mind can get me another step forward. At age 50, I must admit that I've probably learned and done much more than I can actually remember how to still do anymore. However, having seen or done something does stick with me enough to know that I can do a search and find out more and re-learn or re-apply the use of some tools. It's fun for me to do that. I've also been slowly improving how well I save snippets of information and how well I comment code that I write or re-work in scripts so I can find them and "re-learn" how to do some things.
LEARNING AND RE-LEARNING BY DOING
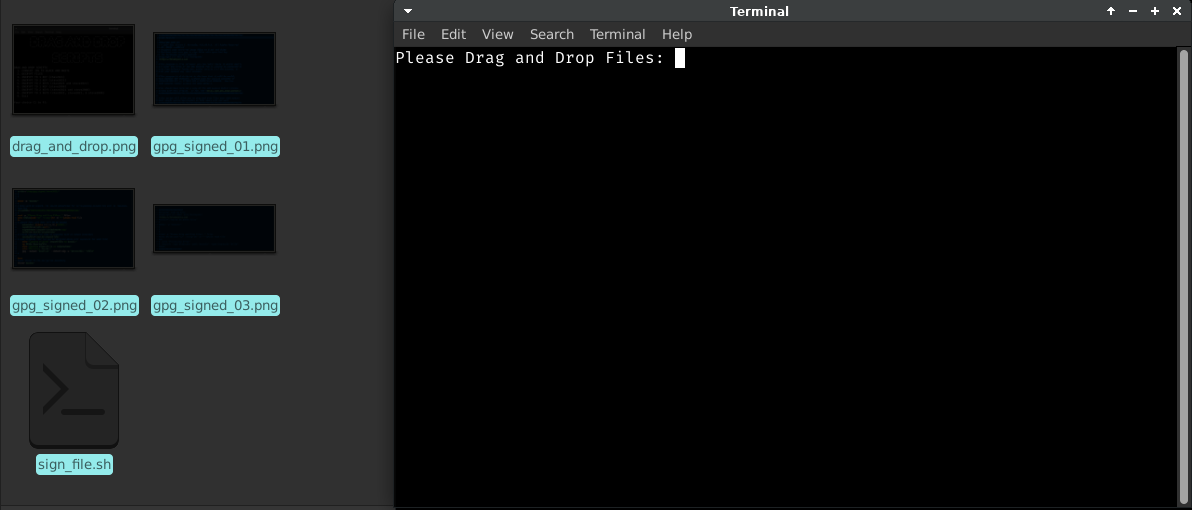
Recently, I wrote about using GNU Privacy Guard and Public Key Infrastructure (GNUPG PKI) for data privacy and encryption. A couple of years ago I was inspired by a BASH script by Kris Occhipinti (Films by Kris) that he wrote and shared. I created a whole menu to run several related adapted scripts to work on files using the command line interface (CLI) or Terminal in GNU/Linux. I'd make a screen capture of the menu, but it's just an enumerated list that allows me to choose a script to do some things. The scripts that I wrote included one that converted a JPG file to Black and White and some scripts to automate using GPG to encrypt to different keys. The cool thing was that I could just drag and drop multiple files into the terminal and have the script work on all of them and output the result to a temporary folder on my computer to allow me to see the results and then copy the files to wherever I wanted to store them.
BULK GPG SIGNING
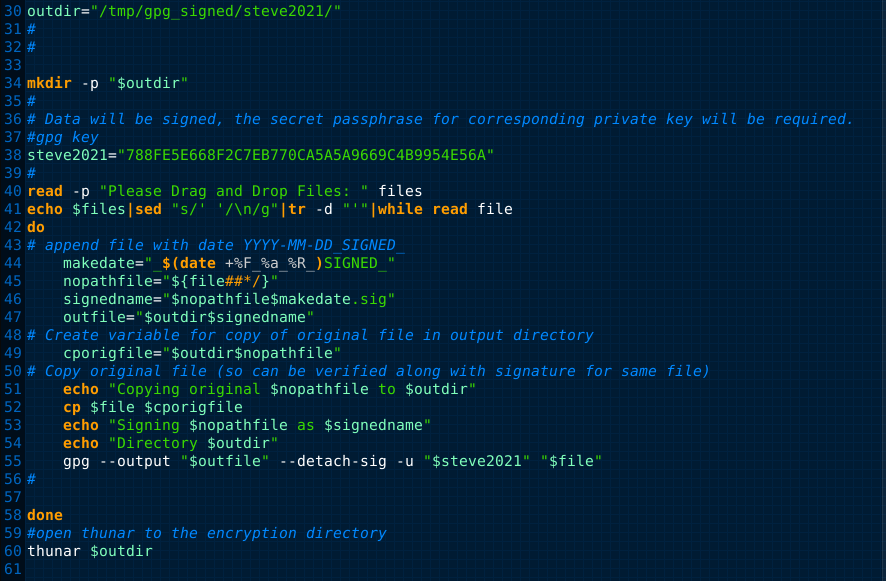
I used one of the bulk encryption scripts from 2 years ago that I wrote and reworked it to allow me to bulk sign files. I love it when I work out the bugs and tweak some code to make a script get something done.
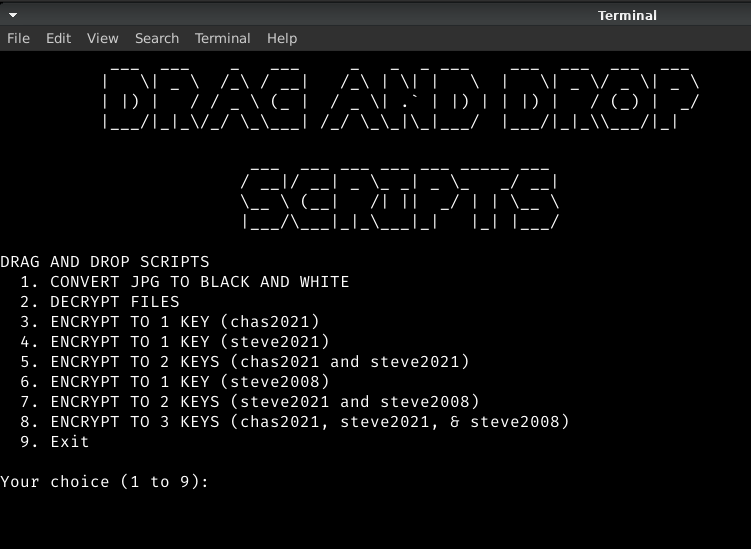

gpg --verify [filename.sig] [filename]
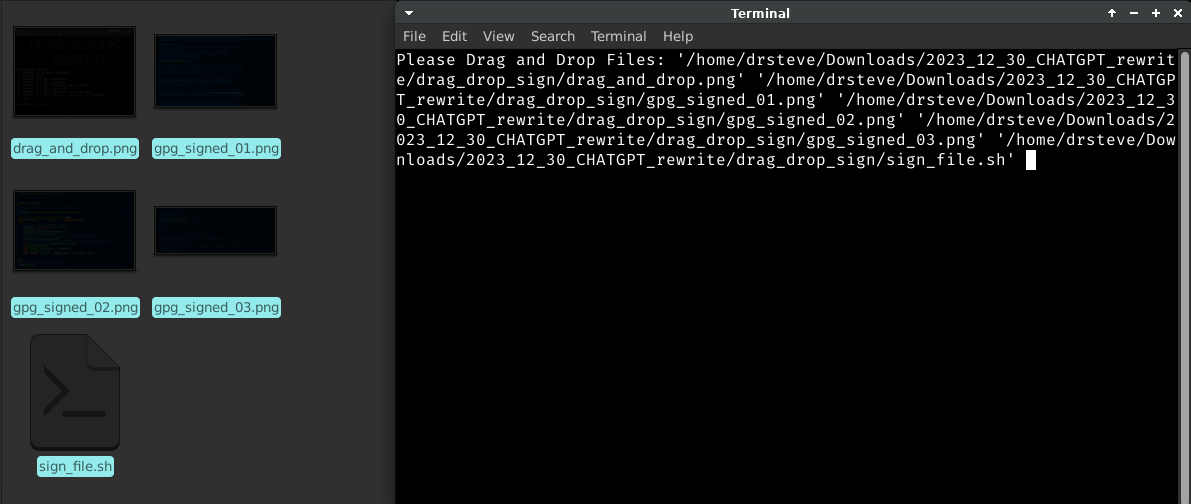
Just replace [filename.sig] with the detached signature file ending in .sig and replace [filename] with the corresponding original filename. This can be done quickly with a drag and drop!
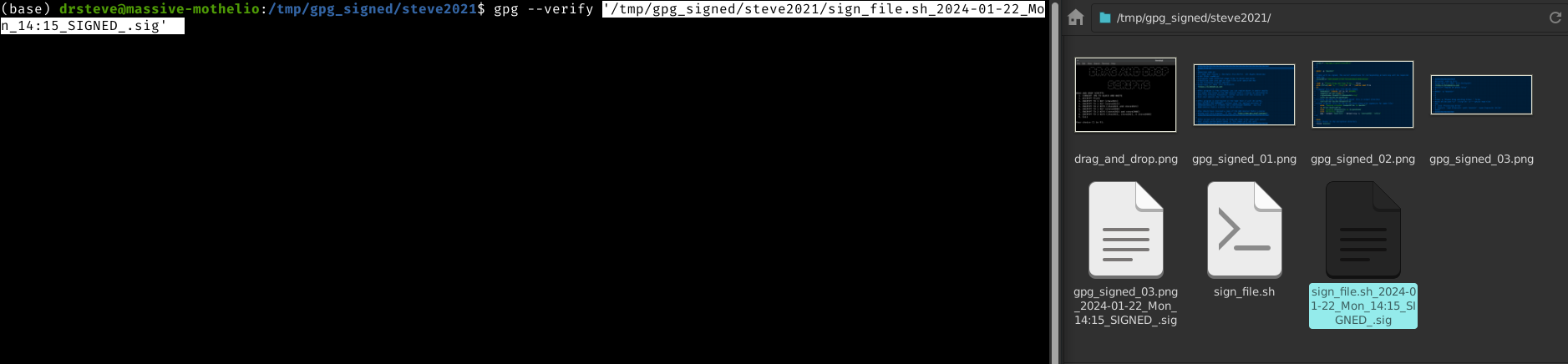
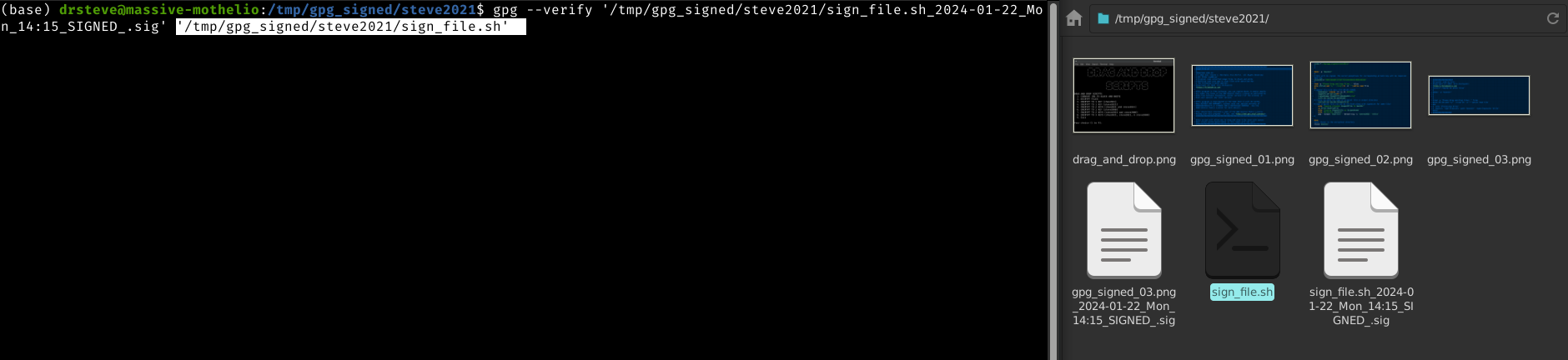
 Verification. Just by pressing ENTER, the gpg will use the detached signature and verify the corresponding file as shown in the prior image.
Verification. Just by pressing ENTER, the gpg will use the detached signature and verify the corresponding file as shown in the prior image.LEARN BY DOING!
Here's a bonus. Did you know that the "cat" or concatenate command can output a file to another file? Well something interesting happens when two files are output into one file in a special situation.
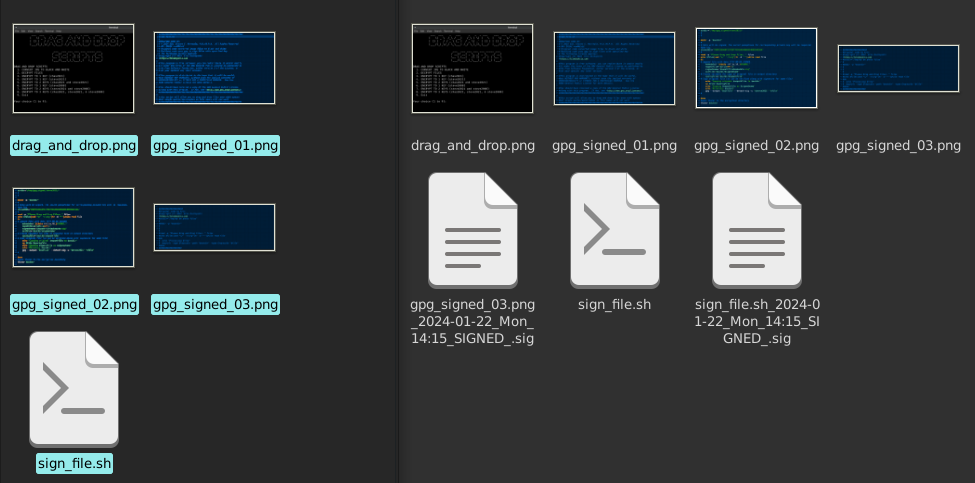
Let's make a "ZIP" file of the images and the script, a README.txt and an INSTRUCTIONS.txt file along with a copy of my public key.
$ zip [ZIPFILENAME] [file1 file2 etc]
We can then use "cat" and an image file, in this case I used a version of one of the ones shown on this page, followed by the ZIPFILENAME created above and output it with ">>" to a new .png file!
The end result is a file that image readers will interpret from the beginning of the file as an image file (and show an image) but "unzip" will interpret from the end of the file as a ".zip" file.
unzip VERIFIED.png
The above command performed on the image on this page called "VERIFIED.png" (if you download it to a new folder on your computer) will extract the packaged files along with their respective detached gpg signatures. I included a README.txt file with the GNU Public License statement for my works inside as well as an INSTRUCTIONS.txt file to show the reader the contents of the ZIP file that were extracted and instructions on making my script "sign_file.sh" executable. You will have to modify the code in the script to make it have a variable (i.e., replace "steve2021" with yours) that will work with your key, and you should probably modify the directory location and name(s) respectively (replace "steve2021" globally for that and the gpg key fingerprint "788FE5E668F2C7EB770CA5A5A9669C4B9954E56A" should be replaced with your key fingerprint). Depending upon your operating system (hopefully a GNU/Linux Distro) you may need to change the file manager that is opening the directory at the end of the script to the one you have installed on your system (or you could add thunar from your package manager). Hope your version of my script ends up working well for you with your key! Test it out and verify any files you sign! If you'd like, send me a copy of your public key and contact information. We can do a key signing after the exchange. See learning by doing isn't that hard now, is it? I think following these recipes is easier than following a recipe in the kitchen... usually a lot less smoke and no smoke alarms going off too!
Have fun and enjoy learning by doing! "H4ppy H4ck1ng"2
⚕ÐɌ ŠŦɆɅɆ
“Leet speak” is often written out with numbers: 1337 5P34K. From this example we can see that the number 1 is used for an L, 3 is used in place of an E, and 7 represents a T. Vowels are often the letters replaced with symbols, but it's not uncommon to see consonants changed as well.
Links:
NOTES: 1 Email Self Defense (https://emailselfdefense.org) - Learn about and use GNU Privacy Guard (gpg) 2 "Happy Hacking" translated to "Basic Leet" at https://www.gamehouse.com/blog/leet-speak-cheat-sheet/ "LEET SPEAK TRANSLATOR"(Given this example, "[-]Д|>|>¥ [-]Д[|{|ท6", I don't think "⚕⚜/ŝčϻ, (⚕ÐɌ ŠŦɆɅɆ ⚜ӍʘɌɌɆѦŁɆ)" is "FULL RETARD LEET" but it may be very close... ROFLMAO!)
